Chrome supports passkeys on iCloud Keychain starting in Chrome 118, on macOS 13.5 or later.
Passkeys are a safer and more user friendly alternative to passwords. They enable users to sign in to apps and websites by unlocking their device screen–with a biometric sensor (such as a fingerprint or facial recognition), PIN, or a pattern. With passkeys, users no longer need to remember and manage passwords. Passkeys are already supported in Chrome across many operating systems.
Until today, passkeys created on macOS were only stored locally in the user's Chrome profile. They were not synchronized, even when they were discoverable credentials.

From Chrome 118, on macOS 13.5 or later, users will have the option to save passkeys in, and use them from, iCloud Keychain. Passkeys stored in iCloud Keychain are synchronized across the Apple ecosystem.
How iCloud Keychain is supported in Chrome
There are no changes required from developers to align their passkey implementation with iCloud Keychain. The API behaviors on Safari and Chrome with iCloud Keychain are identical. Users on Chrome 118 and later on macOS 13.5 or later will see the following changes:
Registration
When creating a new passkey, macOS's system user verification dialog appears. This dialog is the same as Safari's.

The UI varies depending on the supported user verification method on the device such as Apple Watch, Touch ID or a system password. When the user verifies their identity, a new passkey is created and saved to iCloud Keychain.
iCloud Keychain synchronizes the saved passkey to other Apple devices that run macOS, iOS, or iPadOS where the user is signed in using the same iCloud account, so that they can use the passkey to sign in to the websites and apps.
Passkeys stored in iCloud Keychain are available to different browsers as well. For example, a passkey created on Safari can be available in Chrome on macOS and vice versa.
Authentication
Users can also sign in to your website using the passkey stored in iCloud Keychain.

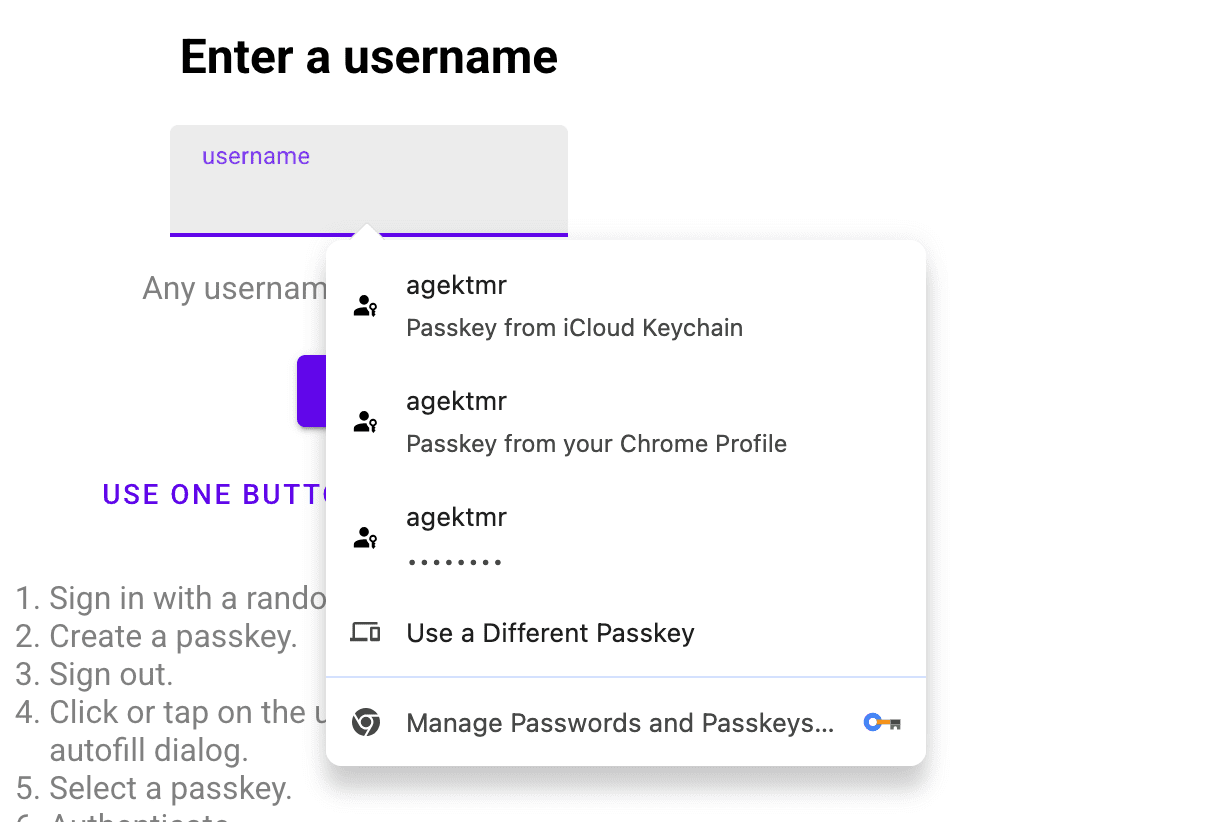
Note that passkeys stored to the Chrome profile previously continue to be available, but ones stored to iCloud Keychain are prioritized. If only a passkey from Chrome profile is available, it will be used to authenticate the user.

If authentication is requested using form autofill (conditional UI), passkeys from iCloud Keychain are listed as part of the autofill suggestions if the user has granted Chrome the necessary permission. If there are passkeys stored in the Chrome profile, they are suggested too.
Saving passkeys to Chrome profile
Even with iCloud Keychain support, users can choose to save passkeys to their Chrome profile by default .
- In Chrome, visit
chrome://password-manager/settings - Turn off the Use passkeys across your Apple devices toggle to explicitly store passkeys to the Chrome profile by default.

Users can also cancel the macOS's user verification dialog and choose iCloud Keychain or Chrome profile to save a new passkey.

Distinguishing the origin of a passkey
Again, there are no changes required from developers to align their passkey implementation with iCloud Keychain. The API behavior between Chrome profile and iCloud Keychain are already identical.
Relying parties can find out the origin of a passkey and distinguish whether it's been created on iCloud Keychain or on Chrome profile, by looking at the AAGUID (an identifier indicating the type of the authenticator) in the credential's authenticator data.
The AAGUID of a passkey created in Chrome profile is:
adce0002-35bc-c60a-648b-0b25f1f05503. In iCloud Keychain it is:
00000000-0000-0000-0000-000000000000 as of September 2023. You can find known
AAGUIDs in the crowd sourced AAGUID repository.
iCloud Keychain activation
Users must grant Chrome the permission to use iCloud Keychain on macOS the first time they try.
If a user tries to use iCloud Keychain passkeys but is not signed into iCloud or does not have iCloud Keychain syncing enabled, they are directed to System Settings.


